How users connect with the Citrix Secure Access agent
Citrix Gateway operates as follows:
- When users attempt to access network resources across the VPN tunnel, the Citrix Secure Access agent encrypts all network traffic destined for the organization’s internal network and forwards the packets to Citrix Gateway.
- Citrix Gateway terminates the SSL tunnel, accepts any incoming traffic destined for the private network, and forwards the traffic to the private network. Citrix Gateway sends traffic back to the remote computer over a secure tunnel.
When users type the web address, they receive a logon page where they enter their credentials and log on. If the credentials are correct, Citrix Gateway finishes the handshake with the user device.
If the user is behind a proxy server, the user can specify the proxy server and authentication credentials. For more information, see Enabling Proxy Support for User Connections.
The Citrix Secure Access agent is installed on the user device. After the first connection, if users log on by using a Windows-based computer, they can use the icon in the notification area to establish the connection.
Establish the secure tunnel
When users connect with the Citrix Secure Access agent, Secure Hub, or Citrix Workspace app, the client software establishes a secure tunnel over port 443 (or any configured port on Citrix Gateway) and sends authentication information. When the tunnel is established, Citrix Gateway sends configuration information to the Citrix Secure Access agent, Secure Hub, or Citrix Workspace app describing the networks to be secured and containing an IP address if you enable address pools.
Tunnel private network traffic over secure connections
When the Citrix Secure Access agent starts and the user is authenticated, all network traffic destined for specified private networks is captured and redirected over the secure tunnel to Citrix Gateway. Citrix Workspace app must support the Citrix Secure Access agent to establish the connection through the secure tunnel when users log on.
Secure Hub, Secure Mail, and WorxWeb use Micro VPN to establish the secure tunnel for iOS and Android mobile devices.
Citrix Gateway intercepts all network connections that the user device makes and multiplexes them over Secure Sockets Layer (SSL) to Citrix Gateway, where the traffic is demultiplexed and the connections are forwarded to the correct host and port combination.
The connections are subject to administrative security policies that apply to a single application, a subset of applications, or an entire intranet. You specify the resources (ranges of IP address/subnet pairs) that remote users can access through the VPN connection.
The Citrix Secure Access agent intercepts and tunnels the following protocols for the defined intranet applications:
- TCP (all ports)
- UDP (all ports)
- ICMP (types 8 and 0 - echo request/reply)
Connections from local applications on the user device are securely tunneled to Citrix Gateway, which reestablishes the connections to the target server. Target servers view connections as originating from the local Citrix Gateway on the private network, thus hiding the user device. This is also called reverse Network Address Translation (NAT). Hiding IP addresses adds security to source locations.
Locally, on the user device, all connection-related traffic, such as SYN-ACK, PUSH, ACK, and FIN packets, is recreated by the Citrix Secure Access agent to appear from the private server.
Connect through firewalls and proxies
Users of the Citrix Secure Access agent are sometimes located inside another organization’s firewall, as shown in the following figure:
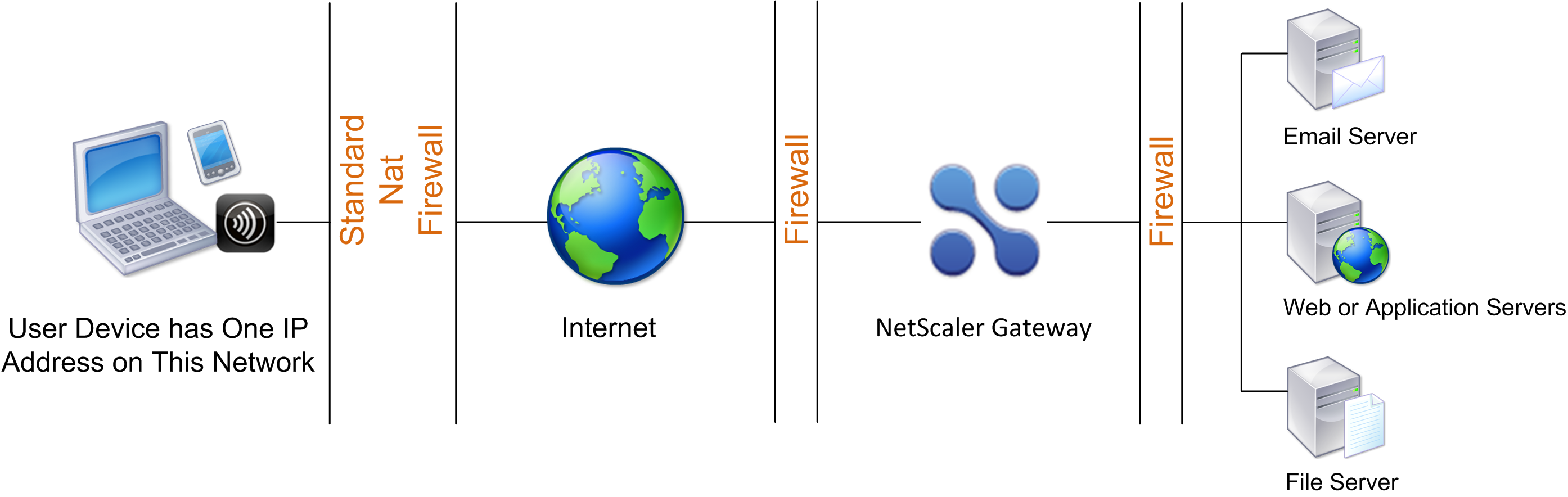
NAT firewalls maintain a table that allows them to route secure packets from Citrix Gateway back to the user device. For circuit-oriented connections, Citrix Gateway maintains a port-mapped, reverse NAT translation table. The reverse NAT translation table enables Citrix Gateway to match connections and send packets back over the tunnel to the user device with the correct port numbers so that the packets return to the correct application.
Control upgrade of Citrix Secure Access agents
System Administrators control how the Citrix ADC plug-in performs when its version does not match the Citrix Gateway revision. The new options control the plug-in upgrade behavior for Mac, and Windows or operating systems.
For VPN plug-ins, the upgrade option can be set in two places in the Citrix ADC appliance user interface:
- At the Global Settings
- At the Session Profile level
Requirements
-
Windows EPA and VPN plug-in version must be greater than 11.0.0.0
-
Mac EPA plug-in version must be greater than 3.0.0.31
-
Mac VPN plug-in version must be greater than 3.1.4 (357)
Note:
If the Citrix ADC appliance is upgraded to the 11.0 release, all previous VPN (and EPA) plug-ins upgrade to the latest version irrespective of upgrade control configuration. For subsequent upgrades, they respect the previous upgrade control configuration.
Plug-in behaviors
For each client type, Citrix Gateway allows the following three options to control plug-in upgrade behavior:
- Always
The plug-in always gets upgraded whenever the end user’s plug-in version doesn’t match with the plug-in shipped with the Citrix ADC appliance. This is the default behavior. Choose this option if you don’t want multiple plug-in versions running in your enterprise.
- Essential (and security)
The plug-in only upgraded when it is deemed necessary. Upgrades are deemed necessary in the following two circumstances
-
Installed Plug-in is incompatible with the current Citrix ADC appliance version.
-
Installed Plug-in must be updated for the necessary security fix.
Choose this option if you want to minimize the number of plug-in upgrades, but don’t want to miss any plug-in security updates
- Never
The plug-in does not get upgraded.
CLI parameters for controlling VPN plug-in upgrade
Citrix Gateway supports two types of plug-ins (EPA and VPN) for Windows and Mac operating systems. To support VPN plug-in upgrade control at the session level, Citrix Gateway supports two session profile parameters named WindowsinPluginUpgrade and MacPluginUpgrade.
These parameters are available at global, virtual server, group, and user level. Each parameter can have a value of Always, Essential or Never. For a description of these parameters see Plug-in Behaviors.
CLI parameters for controlling EPA plug-in upgrade
Citrix Gateway supports EPA plug-ins for Windows and Mac operating systems. To support EPA plug-in upgrade control at the virtual server level, Citrix Gateway supports two virtual server parameters named windowsEPAPluginUpgrade and macEPAPluginUpgrade.
The parameters are available at the virtual server level. Each parameter can have a value of Always, Essential or Never. For a description of these parameters see Plug-in Behaviors
VPN configuration
Follow these steps for the VPN configuration of Windows, Linux, and Mac plug-ins.
-
Go to Citrix ADC > Policies > Session.
-
Select the desired session policy, and then click Edit.
-
Select the Client Experience tab.
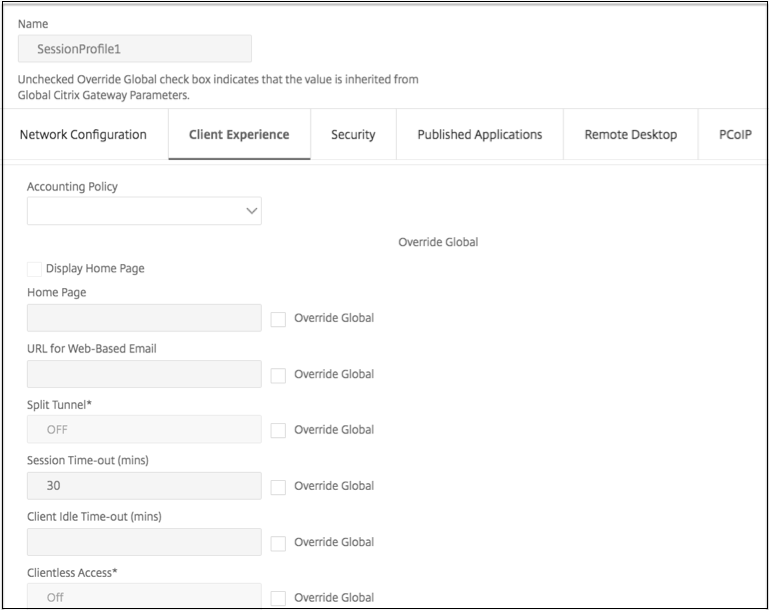
-
These dialog boxes options affect the upgrade behavior.
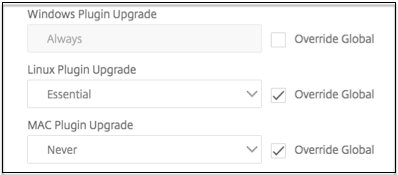
- Always
- Essential
- Never The default is Always.
-
Select the check box to the right of each option. Select the frequency to apply the upgrade behavior.
EPA configuration
Follow these steps for the EPA configuration of Windows, Linux, and Apple plug-ins.
-
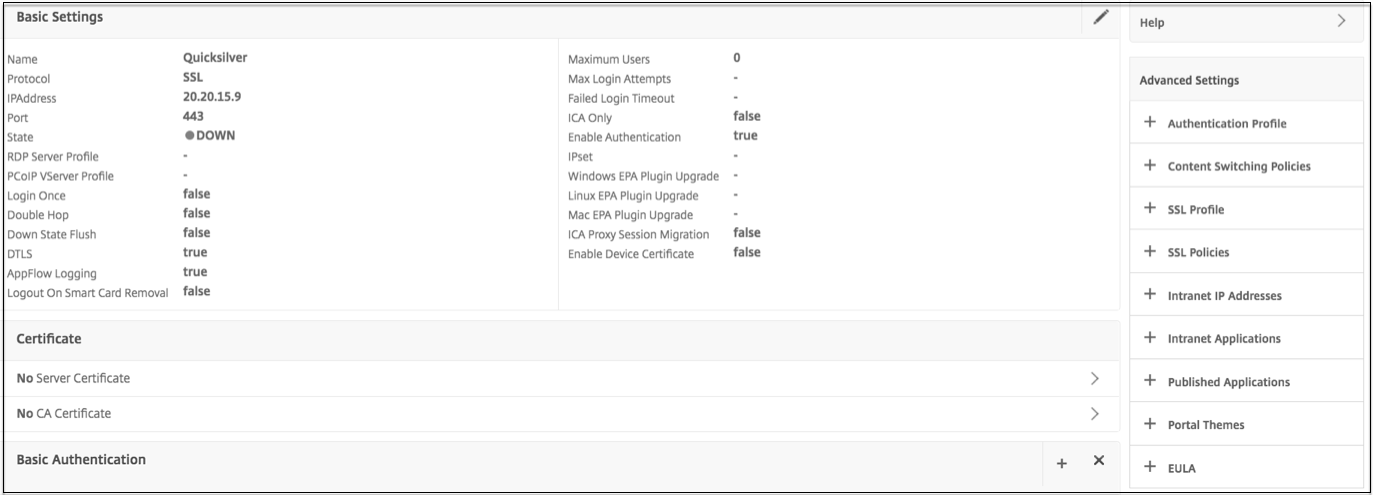
Go to Citrix Gateway > Virtual Servers.
-
Select a server and click the Edit button.
-
Click the pencil icon.
-
Click More
-
The dialog boxes that appear affect the upgrade behavior. The available options are:
- Always
- Essential
- Never
