Set up Citrix SSO for iOS users
IMPORTANT:
Citrix VPN cannot be used on iOS 12 and later. To continue to VPN, use the Citrix SSO app.
For the list of some commonly used features supported by the Citrix SSO for iOS, see Citrix Gateway VPN clients and supported features.
Compatibility with MDM products
Citrix SSO (iOS) and Citrix Secure Access (macOS) are compatible with most MDM providers such as Citrix Endpoint Management (formerly XenMobile), Microsoft Intune and so on.
Citrix SSO (iOS) and Citrix Secure Access (macOS) also support a feature called Network Access Control (NAC). For more information on NAC, see Configure Network Access Control device check for Citrix Gateway virtual server for single factor login. With NAC, MDM administrators can enforce end user device compliance before connecting to the Citrix ADC appliance. NAC on Citrix SSO (iOS) and Citrix Secure Access (macOS) requires an MDM server such as Citrix Endpoint Management or Intune and Citrix ADC.
Note:
To use the Citrix SSO app on iOS or the Citrix Secure Access agent on macOS with Citrix Gateway VPN without MDM, you must add a VPN configuration. You can add the VPN configuration on iOS from the Citrix SSO (iOS) and the Citrix Secure Access (macOS) home page.
Configure an MDM managed VPN profile for Citrix SSO app (iOS) or Citrix Secure Access agent (macOS)
The following section captures step-by-step instructions to configure both device-wide and per-app VPN profiles for the Citrix SSO app (iOS) or the Citrix Secure Access agent (macOS) using Citrix Endpoint Management (formerly XenMobile) as an example. Other MDM solutions can use this document as reference when working with Citrix SSO (iOS) and Citrix Secure Access (macOS).
Note:
This section explains the configuration steps for a basic Device-wide and Per-App VPN profile. Also you can configure On-Demand, Always-On, Proxies by following the Citrix Endpoint Management (formerly XenMobile) documentation or Apple’s MDM VPN payload configuration.
Device level VPN profiles
Device level VPN profiles are used to set up a system wide VPN. Traffic from all apps and services is tunneled to Citrix Gateway based on the VPN policies (such as Full-tunnel, Split-tunnel, Reverse Split tunnel) defined in Citrix ADC.
To configure a device level VPN on Citrix Endpoint Management
Perform the following steps to configure a device level VPN on Citrix Endpoint Management.
-
On the Citrix Endpoint Management MDM console, navigate to Configure > Device Policies > Add New Policy.
-
Select iOS on the left Policy Platform pane. Select VPN on the right pane.
-
On the Policy Info page, enter a valid policy name and description and click Next.
-
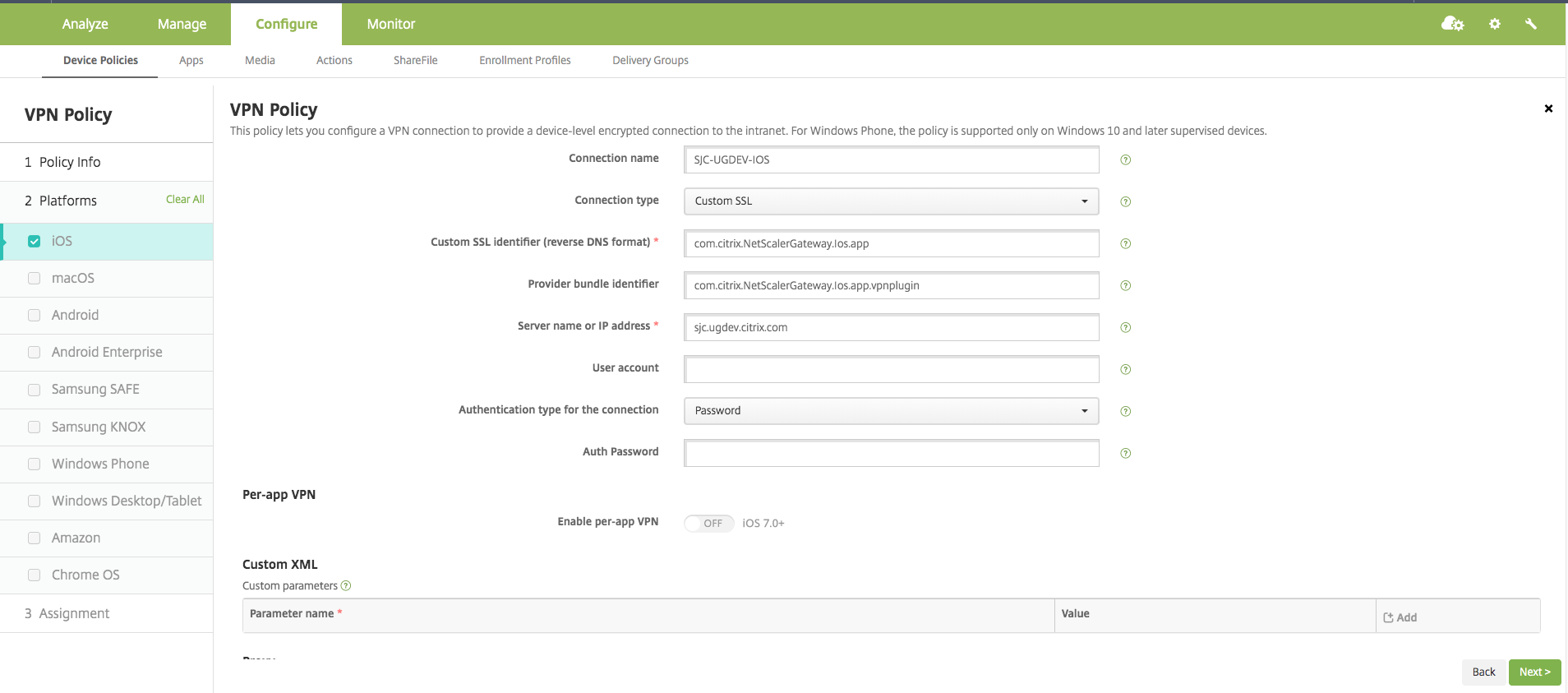
On the VPN Policy page for iOS, type a valid connection name and choose Custom SSL in Connection Type.
In the MDM VPN payload, the connection name corresponds to the UserDefinedName key and VPN Type Key must be set to VPN.
-
In Custom SSL identifier (reverse DNS format), enter com.citrix.NetScalerGateway.ios.app. This is the bundle identifier for the Citrix SSO App on iOS.
In the MDM VPN payload, the Custom SSL identifier corresponds to the VPNSubType key.
-
In Provider bundle identifier enter com.citrix.NetScalerGateway.ios.app.vpnplugin. This is the bundle identifier of the network extension contained in the Citrix SSO iOS app binary.
In the MDM VPN payload, the provider bundle identifier corresponds to the ProviderBundleIdentifier key.
-
In Server name or IP address enter the IP address or FQDN (fully qualified domain name) of the Citrix ADC associated with this Citrix Endpoint Management instance.
The remaining fields in the configuration page are optional. Configurations for these fields can be found in the Citrix Endpoint Management (formerly XenMobile) documentation.
-
Click Next.
-
Click Save.
Per-App VPN profiles
Per-App VPN profiles are used to set up the VPN for a specific application. Traffic from only the specific app is tunneled to Citrix Gateway. The Per-App VPN payload supports all keys for Device-wide VPN plus a few other keys.
To configure a per-App level VPN on Citrix Endpoint Management
Perform the following steps to configure a Per-App VPN:
-
Complete the device level VPN configuration on Citrix Endpoint Management.
-
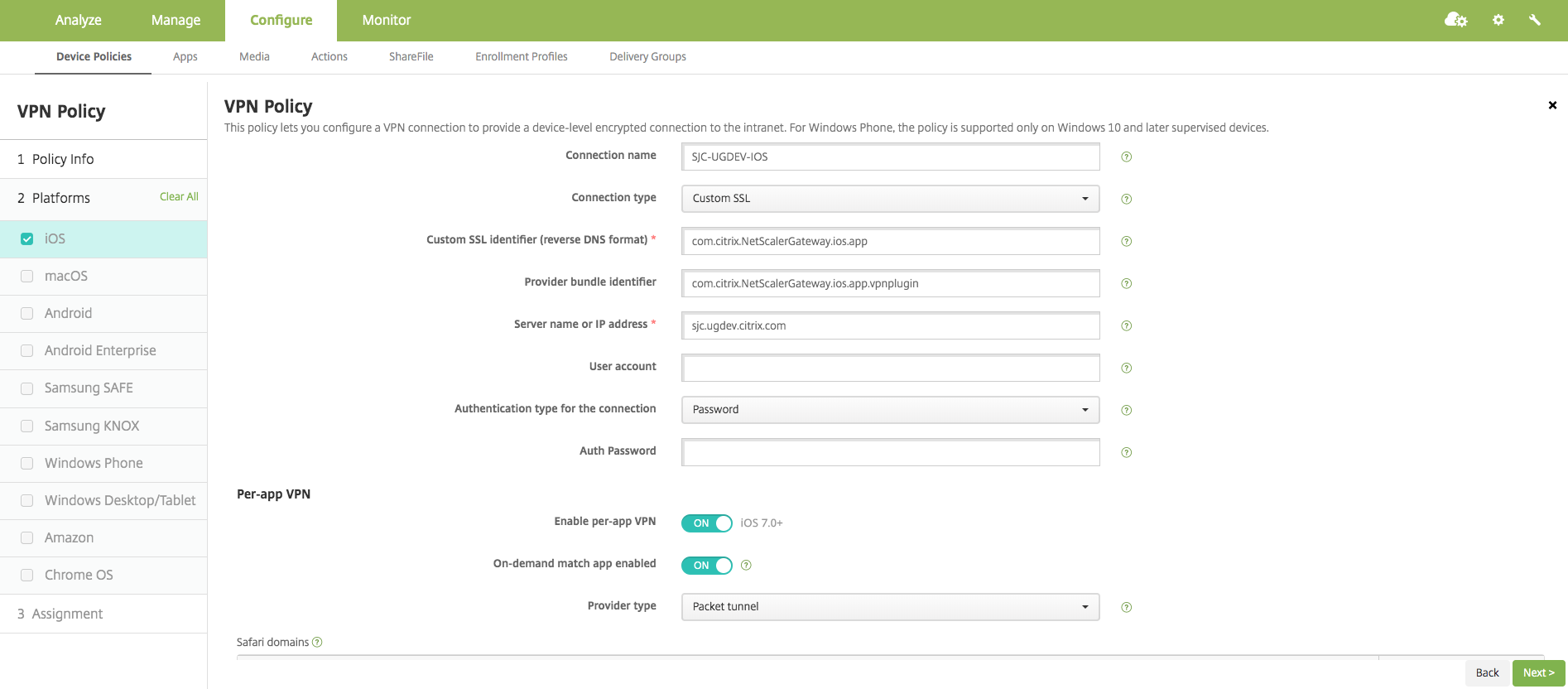
Turn the Enable Per-App VPN switch ON in the Per-App VPN section.
-
Turn the On-Demand Match App Enabled switch ON if Citrix SSO (iOS) and Citrix Secure Access (macOS) must be started automatically when the Match App is launched. This is recommended for most Per-App cases.
In the MDM VPN payload, this field corresponds to the key OnDemandMatchAppEnabled.
-
In Provider Type, select Packet Tunnel.
In the MDM VPN payload, this field corresponds to the key Provider Type.
-
Safari Domain configuration is optional. When a Safari domain is configured, Citrix SSO (iOS) and Citrix Secure Access (macOS) starts automatically when users launch Safari and navigate to a URL that matches the one in the Domain field. This is not recommended if you want to restrict the VPN for a specific app.
In the MDM VPN payload, this field corresponds to the key SafariDomains.
The remaining fields in the configuration page are optional. Configurations for these fields can be found in the Citrix Endpoint Management (formerly XenMobile) documentation.
-
Click Next.
-
Click Save.
To associate this VPN profile to a specific App on the device, you must create an App Inventory policy and a credentials provider policy by following this guide - https://www.citrix.com/blogs/2016/04/19/per-app-vpn-with-xenmobile-and-citrix-vpn/.
Configuring split tunnel in Per-App VPN
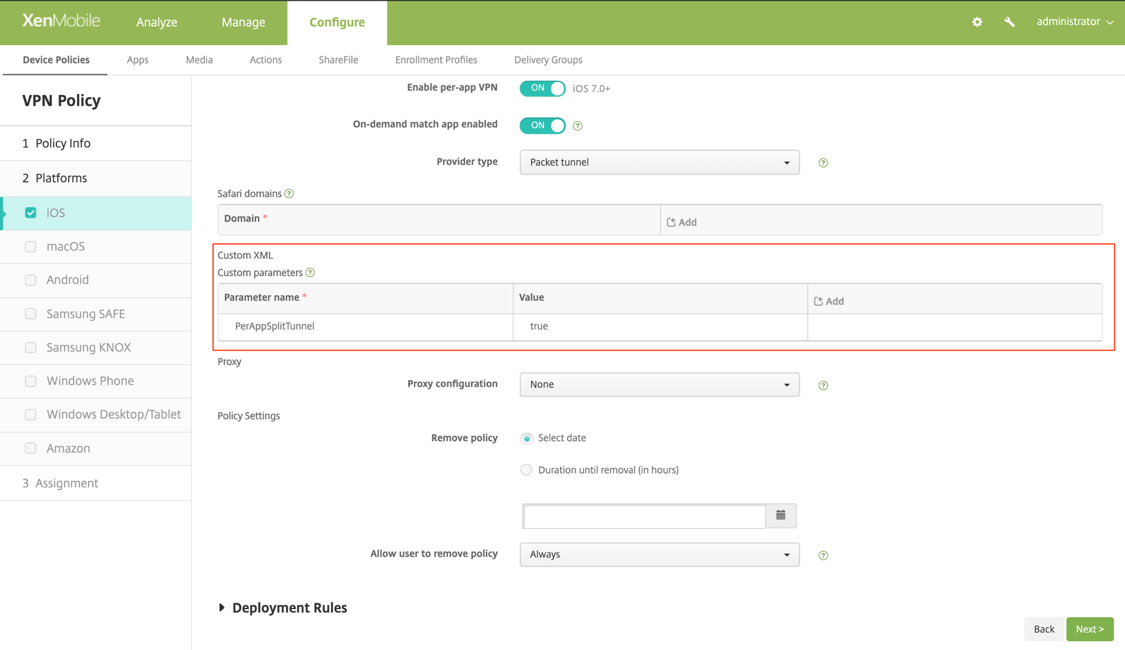
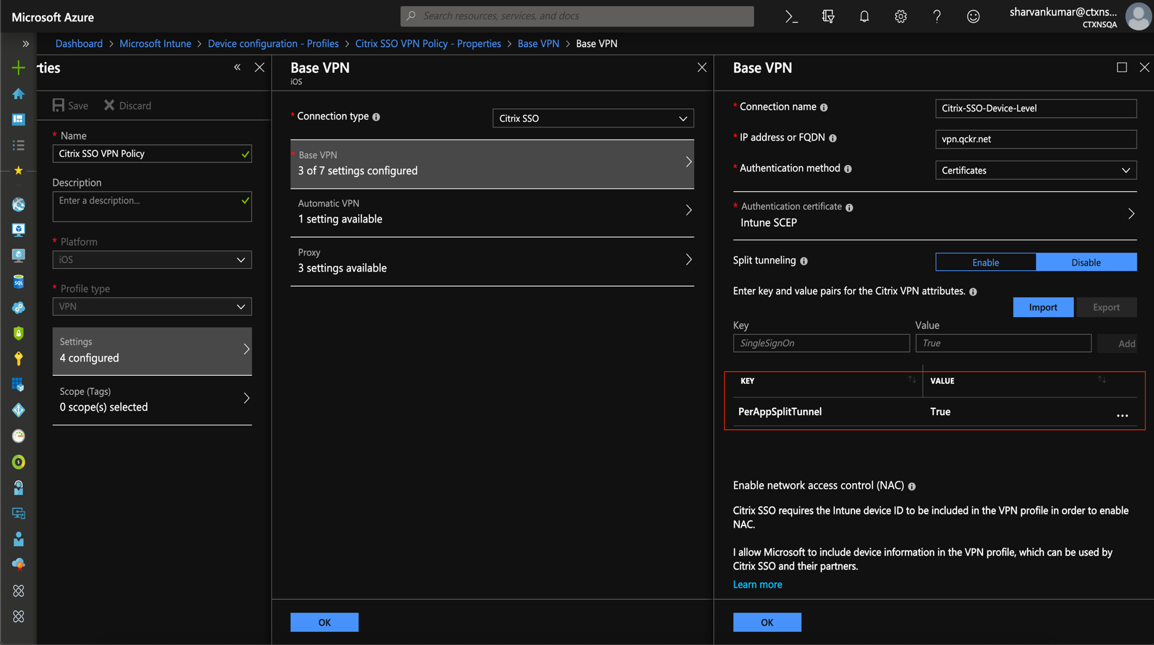
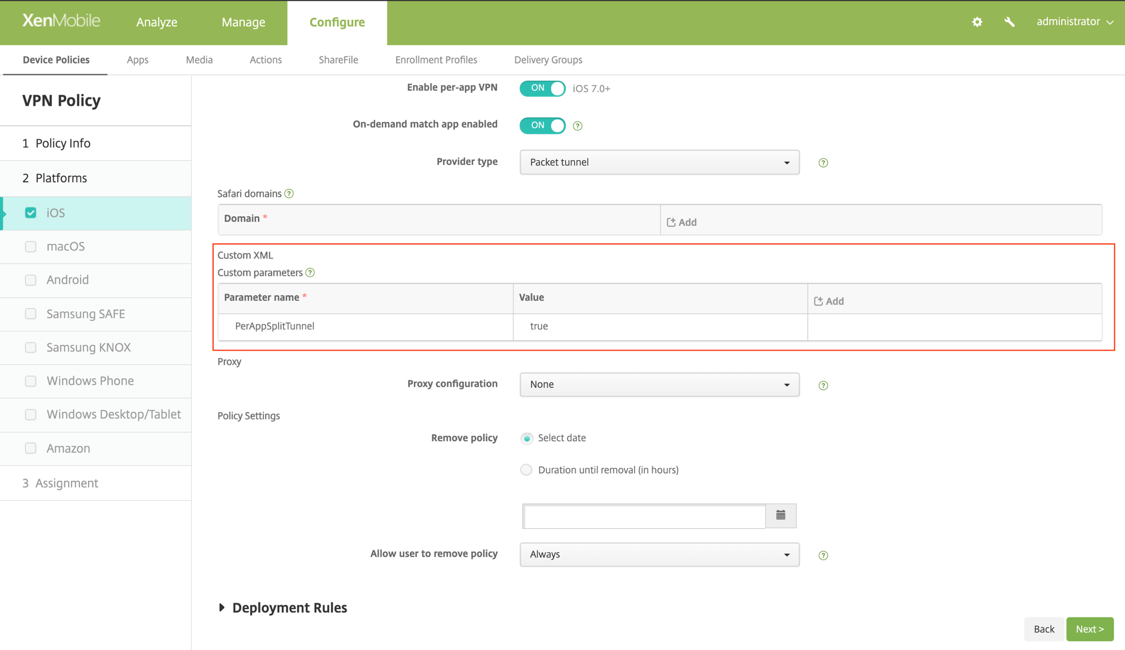
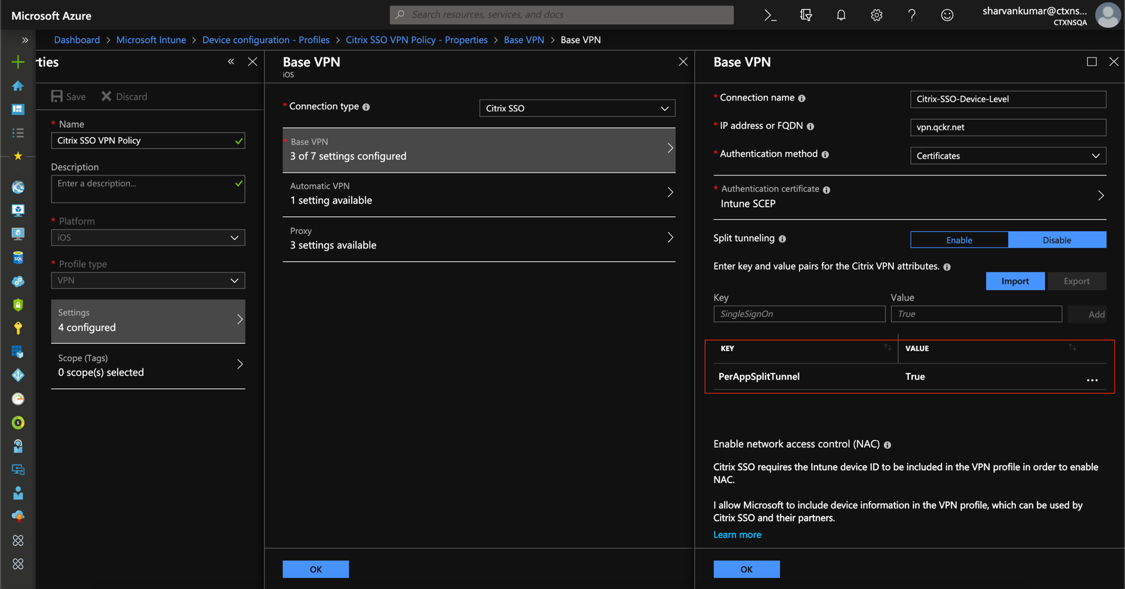
MDM customers can configure split tunnel in Per-App VPN for Citrix SSO (iOS) and Citrix Secure Access (macOS). The following key/value pair must be added to the vendor configuration section of the VPN profile created on the MDM server.
- Key = "PerAppSplitTunnel"
- Value = "true or 1 or yes"
<!--NeedCopy-->
The key is case sensitive and must be an exact match while the value is not case sensitive.
Note:
The user interface to configure vendor configuration is not standard across MDM vendors. Contact the MDM vendor to find the vendor configuration section on your MDM user console.
The following is a sample screenshot of the configuration (vendor specific settings) in Citrix Endpoint Management.
The following is a sample screenshot of the configuration (vendor specific settings) in Microsoft Intune.
Disabling user created VPN profiles
MDM customers can prevent users from manually creating VPN profiles from within the Citrix SSO (iOS) app and Citrix Secure Access (macOS) agent. To do this, the following key/value pair must be added to the vendor configuration section of the VPN profile created on the MDM server.
- Key = "disableUserProfiles"
- Value = "true or 1 or yes"
<!--NeedCopy-->
The key is case sensitive and must be an exact match while the value is not case sensitive.
Note:
The user interface to configure vendor configuration is not standard across MDM vendors. Contact the MDM vendor to find the vendor configuration section on your MDM user console.
The following is a sample screenshot of the configuration (vendor specific settings) in Citrix Endpoint Management.
The following is a sample screenshot of the configuration (vendor specific settings) in Microsoft Intune.
DNS handling
The recommended DNS settings for the Citrix SSO app or the Citrix Secure Access agent are as follows:
- Split DNS > REMOTE if split tunnel is set to OFF.
- Split DNS > BOTH if split tunnel is set to ON. In this case, the admins have to add DNS suffixes for the intranet domains. DNS queries for FQDNs belonging to DNS suffixes are tunneled to the Citrix ADC appliance and the remaining queries go to the local router.
Note:
It is recommended that the DNS truncate fix flag is always ON. For more details, see https://support.citrix.com/article/CTX200243.
When split tunnel is set to ON and split DNS is set to REMOTE, there might be issues resolving DNS queries after the VPN is connected. This is related to the Network Extension framework not intercepting all the DNS queries.
Known issues
Issue description: Tunneling for FQDN addresses that contain a “.local” domain in Per-App VPN or On-Demand VPN configurations. There is a bug in Apple’s Network Extension framework which stops FQDN addresses containing .local in the domain part (for example, http://wwww.abc.local) from being tunneled over the system’s TUN interface. The traffic for this address is sent out via the device’s physical interface instead. The issue is observed only with Per-App VPN or On-Demand VPN config and is not seen with system-wide VPN configurations. Citrix has filed a radar bug report with Apple, and Apple had noted that according to RFC-6762: https://tools.ietf.org/html/rfc6762, local is a multicast DNS (mDNS)
query and is hence not a bug. However, Apple has not closed the bug yet and it is not clear if the issue will be addressed in future iOS releases.
Workaround: Assign a non .local domain name for such addresses as the workaround.
Limitations
- End point Analysis (EPA) is not supported on iOS.
- Split tunneling based on ports/protocols is not supported.