To configure SAML authentication
-
In the configuration utility, on the Configuration tab, expand Citrix Gateway > Policies > Authentication.
-
In the navigation pane, click SAML.
-
In the details pane, click Add.
-
In the Create Authentication Policy dialog box, in Name, type a name for the policy.
-
Next to Server, click New.
-
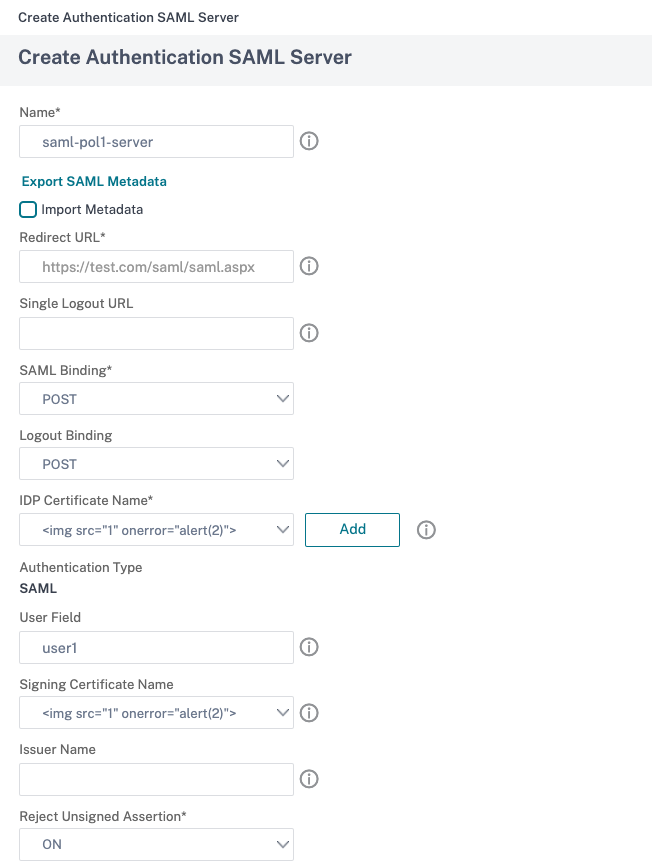
In Name, type a name for the server profile.
-
In IdP Certificate Name, select a certificate or click Install. This is the certificate installed on the SAML or IdP server.
If you click Install, add the certificate and private key. For more information, see Installing and Managing Certificates.
-
In Redirect URL, enter the URL of the authentication Identity Provider (IdP).
This is the URL for the user logon to the SAML server. This is the server to which Citrix Gateway redirects the initial request.
-
In Single Logout URL, specify the URL so that the appliance can recognize when to send the client back to the IdP to complete the sign-out process.
-
In SAML Binding, select the method that is to be used to move the client from the SP to the IdP. This needs to be the same on the IdP so that it understands how the client connects to it. When the appliance acts as an SP, it supports POST, REDIRECT, and ARTIFACT bindings.
-
In Logout Binding, select REDIRECT.
-
In IDP Certificate Name, select the IdPCert Certificate (Base64) present under the SAML Signing Certificate.
Note:
You can also click Import Metadata and select the URL where the metadata configuration is stored.
-
In User Field, enter the user name to extract.
-
In Signing Certificate Name, Select the SAML SP certificate (with private key) that the appliance uses to sign authentication requests to the IdP. The same certificate (without private key) must be imported to the IdP, so that the IdP can verify the authentication request signature. This field is not needed by most IdPs
This is the certificate that is bound to the Citrix Gateway virtual IP address. The SAML Issuer Name is the fully qualified domain name (FQDN) to which users log on, such as lb.example.com or ng.example.com.
-
In Issuer Name, enter the FQDN of the load balancing or Citrix Gateway virtual IP address to which the appliance sends the initial authentication (GET) request.
-
In Reject unsigned assertion, specify if you require the Assertions from the IdP to be signed. You can ensure that only the Assertion must be signed (ON) or both the assertion and the response from the IdP must be signed (STRICT).
-
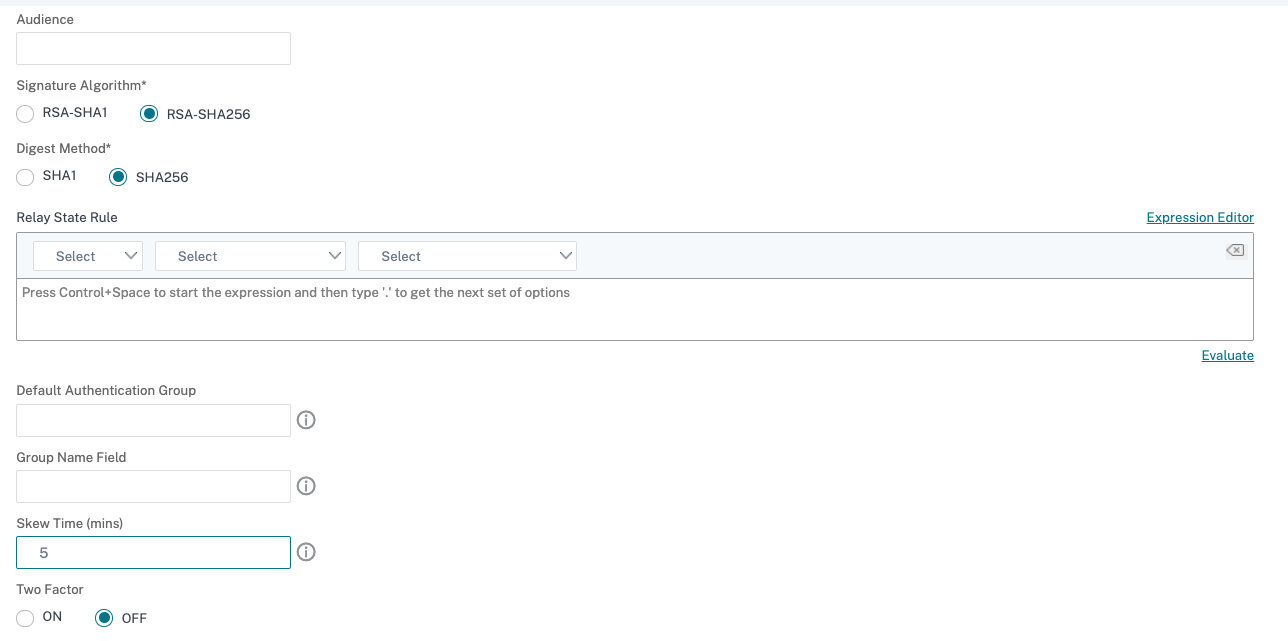
In Audience, enter the audience for which the assertion sent by IdP is applicable. This is typically an entity name or URL that represents the service provider.
-
In Signature Algorithm, select RSA-SHA256
-
In Digest Method, select SHA256
-
In Default Authentication Group, enter the default group that is chosen when the authentication succeeds in addition to the extracted groups.
-
In Group Name, enter the name of the tag in the assertion that contains user groups.
-
In Skew Time (mins), specify the allowed clock skew in minutes that the service provider allows on an incoming assertion.
-
Click Create, and then click Close.
-
In the Create authentication policy dialog box, next to Named Expressions, select General, select True value, click Add Expression, click Create, and then click Close.