Select the Citrix Secure Access agent for users
When you configure Citrix Gateway, you can choose how users log on. Users can log on with one of the following plug-ins:
- Citrix Secure Access agent for Windows
- Citrix Secure Access agent for macOS
You complete the configuration by creating a session policy and then binding the policy to users, groups, or virtual servers. You can also enable plug-ins by configuring global settings. Within the global or session profile, you select either Windows or macOS X as the plug-in type. When users log on, they receive the plug-in as defined globally or in the session profile and policy. Create separate profiles for the plug-in type.
Configure the plug-in globally
- In the configuration utility, on the Configuration tab, in the navigation pane, expand Citrix Gateway and then click Global Settings.
- In the details pane, under Settings, click Change global settings.
- On the Client Experience tab, next to plug-in Type, select Windows/macOS X and then click OK.
Configure the plug-in type for Windows or macOS in a session profile
- In the configuration utility, on the Configuration tab, in the navigation pane, expand Citrix Gateway > Policies and then click Session.
- Do one of the following:
- If you are creating a session policy, in the details pane, click Add.
- If you are changing an existing policy, select a policy, and then click Open.
- Create a profile or modify an existing profile. To do so, do one of the following:
- Next to Request Profile, click New.
- Next to Request Profile, click Modify.
- On the Client Experience tab, next to plug-in Type, click Override Global and then select Windows/macOS X.
- Do one of the following:
- If you are creating a profile, click Create, set the expression in the policy dialog box, click Create, and then click Close.
- If you are modifying an existing profile, after making the selection, click OK twice.
Citrix Secure Access agent for Windows
When users log on to Citrix Gateway, they download and install the Citrix Secure Access agent on the user device.
To install the plug-in, users must be a local administrator or a member of the Administrators group. This restriction applies for first-time installation only. Plug-in upgrades do not require administrator level access.
To enable users to connect to and use Citrix Gateway, you need to provide them with the following information:
- Citrix Gateway web address, such as https://NetScalerGatewayFQDN/
- Any system requirements for running the Citrix Secure Access agent if you configured endpoint resources and policies
Depending on the configuration of the user device, you might also need to provide the following information:
- If users run a firewall on their computer, they must change the firewall settings so that the firewall does not block traffic to or from the IP addresses corresponding to the resources for which you granted access. The Citrix Secure Access agent automatically handles Internet Connection Firewall in Windows XP and Windows Firewall in Windows XP Service Pack 2, Windows Vista, Windows 7, Windows 8, or Windows 8.1.
- Users who want to send traffic to FTP over a Citrix Gateway connection must set their FTP application to perform passive transfers. A passive transfer means that the remote computer establishes the data connection to your FTP server, rather than the establishment of the data connection by the FTP server to the remote computer.
- Users who want to run X client applications across the connection must run an X server, such as
XManager, on their computers. - Users who install Receiver for Windows or Receiver for Mac can start the Citrix Secure Access agent from Receiver or by using a web browser. Provide instructions to users about how to log on with the Citrix Secure Access agent through Receiver or a web browser.
Because users work on files and applications as if they are local to the organization’s network, you do not need to retrain users or configure applications.
To establish a secure connection for the first time, log on to Citrix Gateway by using the web logon page. The typical format of a web address is https://companyname.com. When users log on, they can download and install the Citrix Secure Access agent on their computer.
Install the Citrix Secure Access agent for Windows
- In a web browser, type the web address of Citrix Gateway.
- Type the user name and password and then click Logon.
- Select Network Access and then click Download.
- Follow the instructions to install the plug-in.
When the download is complete, the Citrix Secure Access agent connects and displays a message in the notification area on a Windows-based computer.
If you want users to connect with the Citrix Secure Access agent without using a web browser, you can configure the plug-in to display the logon dialog box when users right-click the Citrix Gateway icon in the notification area on a Windows-based computer or start the plug-in from the Start menu.
Configure the logon dialog box for the Citrix Secure Access agent for Windows
To configure the Citrix Secure Access agent to use the logon dialog box, users must be logged on to complete this procedure.
- On a Windows-based computer, in the notification area, right-click the Citrix Gateway icon and then click Configure Citrix Gateway.
- Click the Profile tab and then click Change Profile.
- On the Options tab, click Use the Citrix Secure Access agent for logon. Note: If users open the Configure Citrix Gateway dialog box from within Receiver, the Options tab is not available.
Set the interception mode for the Citrix Secure Access agent for Windows
If you are configuring the Citrix Secure Access agent for Windows, you also need to configure the interception mode and set it to transparent.
- In the configuration utility, click the Configuration tab, expand Citrix Gateway > Resources, and then click Intranet Applications.
- In the details pane, click Add.
- In Name, type a name for the policy.
- Click Transparent.
- In Protocol, select ANY.
- In Destination Type, select IP Address and Netmask.
- In IP address type the IP address.
- In Netmask, type the subnet mask, click Create, and then click Close.
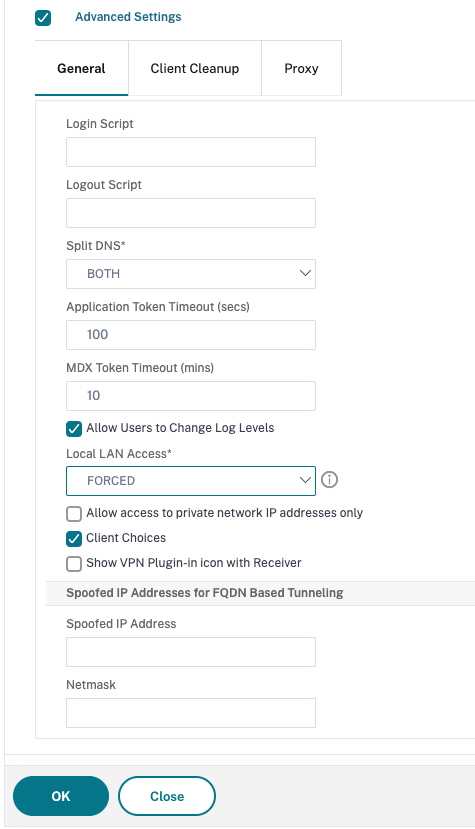
Enforce local LAN access to end users based on ADC configuration
Admins can restrict the end users to enable or disable the local LAN access option on their client machines. A new option, FORCED is added to the existing Local LAN Access parameter values. When the Local LAN Access value is set to FORCED, end users are restricted from using the local LAN access option on their client machines. If the end users need to enable or disable the local LAN access, the admins must reconfigure the Local LAN Access option in the Citrix ADC appliance accordingly.
To enable the Forced option by using the GUI:
- Navigate to Citrix Gateway > Global Settings > Change Global Settings.
- Click the Client Experience tab and then click Advanced Settings.
- In Local LAN Access, select FORCED.
To enable the Forced option by using the CLI, run the following command:
set vpn parameter -localLanAccess FORCED
<!--NeedCopy-->
Microsoft Edge WebView support for Windows Citrix Secure Access – Preview
Microsoft Edge WebView support for Windows Citrix Secure Access introduces an enhanced end user experience. For details, see Microsoft Edge WebView support for Windows Citrix Secure Access
Windows Citrix Secure Access agent using Windows Filtering Platform
The Windows Filtering Platform (WFP) is a set of API and system services that provide a platform for creating network filtering application. WFP is designed to replace previous packet filtering technologies, the Network Driver Interface Specification (NDIS) filter which was used with the DNE driver. The WFP mode is supported with the 22.6.1.5 build of the Windows Citrix Secure Access agent.
Install the WFP build
You can install the WFP build using one of the following methods.
-
Install the VPN plug-in with both the DNE and WFP drivers (default method)
When the plug-in is installed with both the DNE and WFP drivers, admins can use either the WFP or the DNE driver for tunneling via a registry knob. By default, the DNE driver is used for tunneling.
-
Install the VPN plug-in with just the WFP driver (Skip DNE driver installation)
DNE drivers are not supported with some of the third-party applications even when not in use. For those deployments, admins can use this installation type. As the DNE driver is not installed, only the WFP driver is used for tunneling.
Select a WFP driver instead of a DNE driver
Perform the following steps to select the WFP driver instead of the DNE driver.
Note:
This works only with the default installation method.
- Download the WFP supported VPN plug-in build and install the new VPN plug-in.
- By default, the DNE driver is used to tunnel the traffic. To use the WFP driver for tunneling, admins must create the following registry entry:
- REG_PATH - HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client
- REG_TYPE - REG_DWORD
- REG_NAME - EnableWFP
- REG_VALUE – Set value to 1 to use WFP and 0 to use DNE (by default DNE is enabled if this registry value is not present or is set to 0)
- REG_PATH - HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client
Note:
After switching the tunneling mode from DNE to WFP or conversely, the system must be rebooted for the changes to take effect properly.
Completely skip the DNE installation
Perform the following steps to skip the DNE installation.
- Perform a clean uninstallation of the VPN plug-in.
- Uninstall the current VPN plug-in present on the machine and restart the machine.
- Check if the DNE driver is uninstalled using either of the following options.
- Open an elevated command prompt (or PowerShell). Run the following commands (sample output shows that the DNE based driver is installed on the system)
PS C:\Users\Administrator> sc qc cag [SC] QueryServiceConfig SUCCESS SERVICE_NAME: cag TYPE : 1 KERNEL_DRIVER START_TYPE : 2 AUTO_START ERROR_CONTROL : 1 NORMAL BINARY_PATH_NAME : \??\C:\Program Files\Common Files\Deterministic Networks\Common Files\cag.sys LOAD_ORDER_GROUP : TAG : 0 DISPLAY_NAME : Citrix cag plugin for Access Gateway DEPENDENCIES : SERVICE_START_NAME : PS C:\Users\Administrator> sc qc dne [SC] QueryServiceConfig SUCCESS SERVICE_NAME: dne TYPE : 1 KERNEL_DRIVER START_TYPE : 1 SYSTEM_START ERROR_CONTROL : 1 NORMAL BINARY_PATH_NAME : \SystemRoot\system32\DRIVERS\dnelwf64.sys LOAD_ORDER_GROUP : NDIS TAG : 38 DISPLAY_NAME : DNE LightWeight Filter DEPENDENCIES : SERVICE_START_NAME : <!--NeedCopy-->If the driver is not installed, the following output is displayed:
The specified service does not exist as an installed service.
Because the DNE driver (dnelwf64.sys) is also used by other vendors, it might be present even when the Citrix Secure Access agent is not installed on the system. On the other hand, the CAG plug-in is only used by the Citrix Secure Access agent.
-
DNE presence can also be checked by trying to start the CAG and DNE drivers. Open the command prompt using admin rights and run the following commands:
net start cag net start dne <!--NeedCopy-->- If the output message indicates that the services cannot be located (The service name is invalid.), then the plug-in and driver components are uninstalled successfully. In this case, move to step 2.
- If the plug-in and driver components are not uninstalled successfully, run the Cleanup utility on the client machine by following the instructions provided at https://citrix.sharefile.com/d-s829800c3821a4a8f869ad324de6f0332.
- Unzip the Cleanup utility and copy it to a folder.
- Run nsRmSAC.exe from the command prompt.
- Restart the client machine.
-
Create the following registry entries.
- REG_PATH - HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client
- REG_TYPE - REG_DWORD
- REG_NAME - SkipDNE
- REG_VALUE - Set to 1 to make sure that DNE is not installed on the machine
- REG_PATH - HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client
- REG_TYPE - REG_DWORD
- REG_NAME - EnableWFP
- REG_VALUE - Set to 1 to enable WFP (this entry must be created if the DNE installation is skipped)
Note:
- If the registry entries are not created before installation, DNE is installed, by default. Also, you can check the VPN log files to validate whether WFP or DNE is used.
- If DNE installation is skipped, EnableWFP must be set to 1. In this case, you cannot switch to the DNE based plug-in without reinstalling the Citrix Secure Access agent.
- REG_PATH - HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client
- Install the new VPN plug-in.
-
Confirm if the WFP driver is installed on the system. Open an elevated command prompt and run the following command. The sample output shows that the WFP driver is installed on the system.
PS C:\Users\Administrator> sc qc ctxsgwcallout [SC] QueryServiceConfig SUCCESS SERVICE_NAME: ctxsgwcallout TYPE : 1 KERNEL_DRIVER START_TYPE : 1 SYSTEM_START ERROR_CONTROL : 0 IGNORE BINARY_PATH_NAME : \??\C:\Program Files\Citrix\Secure Access Client\ctxsgwcallout.sys LOAD_ORDER_GROUP : TAG : 0 DISPLAY_NAME : Citrix Secure Access Callout Driver DEPENDENCIES : SERVICE_START_NAME : <!--NeedCopy-->
If the driver is not installed, the following output is displayed:
The specified service does not exist as an installed service.
- Restart the client machine.
Advantages of WFP
The following are some of the advantages of WFP if stand-alone WFP driver installation is done on the client.
-
FQDN based reverse split tunnel support: The WFP driver enables support for FQDN based REVERSE split tunneling. It is not supported with the DNE driver. For more details, see Split tunneling options.
-
Wireshark support: DNE does not allow capturing two-way traffic on a client machine because of its linking with the Ethernet/Wi-Fi adapter. This is not an issue with the new WFP driver. Any traffic capture (one-way or two-way) is encrypted and requires SSL keys to decrypt the same.
-
NMAP support: The new WFP driver supports NMAP scanning while the VPN plug-in used to tunnel the traffic, whereas the DNE does not allow NMAP scanning, while the VPN plug-in used to tunnel the traffic.
-
Network speed: In some scenarios, if DNE is installed on a client machine, download and upload speed are affected, which is not the case with WFP.
-
Improved nslookup performance: Sometimes with DNE,
nslookupfails to respond with lesser number of tries, and the same is not observed with WFP. -
Improved iperf performance over UDP: With DNE, some packet loss was observed during scalability tests using iperf over UDP. Packet loss is not observed with WFP.