-
Install and configure the Citrix Gateway appliance
-
Deploy Citrix Gateway in a double-hop DMZ
-
Maintain and monitor Citrix Gateway systems
-
Configure DTLS VPN virtual server using SSL VPN virtual server
-
Integrate Citrix Gateway with Citrix products
-
Integrate Citrix Gateway with Citrix Virtual Apps and Desktops
-
Configure settings for your Citrix Endpoint Management Environment
-
Configure load balancing servers for Citrix Endpoint Management
-
Configure load balancing servers for Microsoft Exchange with Email Security Filtering
-
Configure Citrix Endpoint Management NetScaler Connector (XNC) ActiveSync Filtering
-
Allow Access from mobile devices with Citrix Mobile Productivity Apps
-
Configure domain and security token authentication for Citrix Endpoint Management
-
Configure client certificate or client certificate and domain authentication
-
-
Configuring Settings for Your Citrix Endpoint Management Environment
-
Configuring Load Balancing Servers for Citrix Endpoint Management
-
Configuring Load Balancing Servers for Microsoft Exchange with Email Security Filtering
-
Configuring Citrix Endpoint Management NetScaler Connector (XNC) ActiveSync Filtering
-
Allowing Access from Mobile Devices with Citrix Mobile Productivity Apps
-
Configuring Domain and Security Token Authentication for Citrix Endpoint Management
-
Configuring Client Certificate or Client Certificate and Domain Authentication
-
-
Citrix Gateway Enabled PCoIP Proxy Support for VMware Horizon View
-
Proxy Auto Configuration for Outbound Proxy support for Citrix Gateway
-
Optimizing Citrix Gateway VPN split tunnel for Office365
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Optimizing Citrix Gateway VPN split tunnel for Office365
As organizations are adapting to the remote work options more rapidly than before, the remote access infrastructure must be optimized to facilitate seamless connectivity during increased traffic load conditions.
*Microsoft recommends excluding traffic destined to key Office 365 services from the scope of VPN connection by configuring split tunneling using published IPv4 and IPv6 address ranges. For best performance and most efficient use of VPN capacity, traffic to this dedicated IP address ranges associated with Office 365 Exchange Online, SharePoint Online, and Microsoft Teams (referred to as Optimize category in Microsoft documentation) must be routed directly, outside of the VPN tunnel. Please refer to [Microsoft guidance] <https://docs.microsoft.com/en-us/Office365/Enterprise/office-365-vpn-split-tunnel> for more detailed information about this recommendation.*
Microsoft’s recommendation in Citrix Gateway is achieved by routing the Microsoft provided list of IP addresses directly to the internet for the O365 traffic by using the split tunnel reverse configuration.
The configuration involves the following that can be performed manually by using the GUI or CLI commands.
- Configure split tunnel for reverse configuration
- Configure intranet applications for user access to resources
Configuration by using the GUI
To configure split tunneling by using the GUI
- On the Configuration tab, Navigate to Citrix Gateway > Global Settings.
- In the details pane, under Settings, click Change Global Settings.
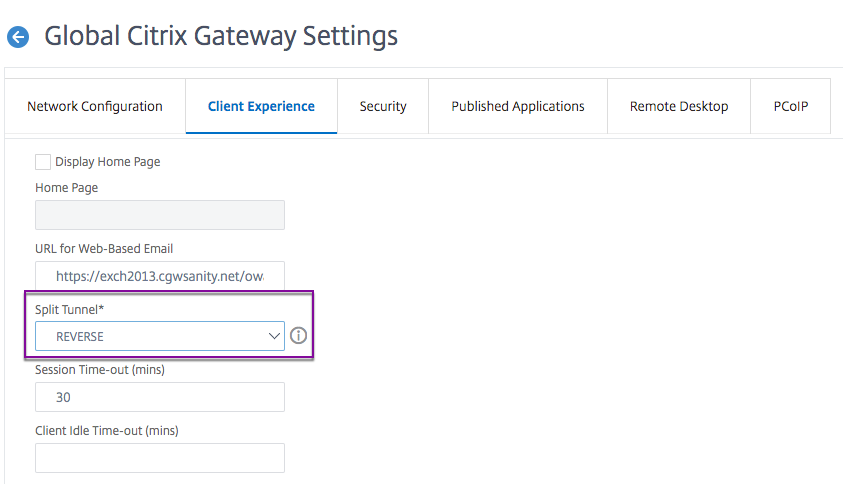
- On the Client Experience tab, in Split Tunnel, select Reverse.
-
Click OK.
To create a VPN intranet application by using the GUI
- On the Configuration tab, Navigate to Citrix Gateway > Global Settings.
- In the details pane, under Intranet Applications, click the link.
-
In the Configure VPN Intranet Application page, click Add, and then click New.
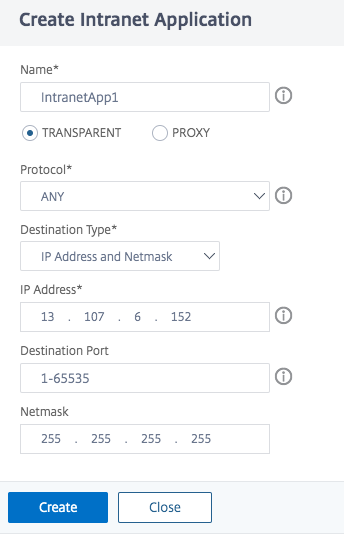
- In Name, type a name for the profile.
- In Protocol, select the protocol that applies to the network resource.
- In Destination Type, select IP Address and Netmask.
- In IP Address, enter the IP address that must be routed directly to the internet for O365 traffic. For the list of IP address, see List of IP addresses.
-
In Netmask, enter the netmask IP address.
- Click Create and then click Close.
Note: Repeat this procedure for all the IP addresses.
Configuration by using the CLI
- To set split tunnel to reverse, at the command prompt, type;
set vpn parameter -splitTunnel REVERSE
<!--NeedCopy-->
- To add VPN intranet application, at the command prompt, type;
add vpn intranetApplication intranetapp1 ANY 13.107.6.152 -netmask 255.255.255.254 -destPort 1-65535 -interception TRANSPARENT
<!--NeedCopy-->
Note: Repeat this procedure for all the IP addresses.
- To bind the intranet application, at the command prompt type;
bind vpn global -intranetApplication intranetapp1
<!--NeedCopy-->
List of IP addresses of Office 365 services (EXO, SPO, and Teams)
Reference: https://docs.microsoft.com/en-us/office365/enterprise/urls-and-ip-address-ranges
Note from Microsoft: As part of Microsoft’s response to the COVID-19 situation, Microsoft has declared a temporary moratorium on some planned URL and IP address changes. This moratorium is intended to provide customer IT teams with confidence and simplicity in implementing recommended network optimizations for work-from-home Office 365 scenarios. From March 24, 2020 through June 30, 2020 this moratorium will halt changes for key Office 365 services (Exchange Online, SharePoint Online, and Microsoft Teams) to IP ranges and URLs included in the Optimize category.
IPv4 address range
104.146.128.0/17
13.107.128.0/22
13.107.136.0/22
13.107.18.10/31
13.107.6.152/31
13.107.64.0/18
131.253.33.215/32
132.245.0.0/16
150.171.32.0/22
150.171.40.0/22
191.234.140.0/22
204.79.197.215/32
23.103.160.0/20
40.104.0.0/15
40.108.128.0/17
40.96.0.0/13
52.104.0.0/14
52.112.0.0/14
52.96.0.0/14
52.120.0.0/14|
IPv6 address range
2603:1006::/40
2603:1016::/36
2603:1026::/36
2603:1036::/36
2603:1046::/36
2603:1056::/36
2603:1096::/38
2603:1096:400::/40
2603:1096:600::/40
2603:1096:a00::/39
2603:1096:c00::/40
2603:10a6:200::/40
2603:10a6:400::/40
2603:10a6:600::/40
2603:10a6:800::/40
2603:10d6:200::/40
2620:1ec:4::152/128
2620:1ec:4::153/128
2620:1ec:c::10/128
2620:1ec:c::11/128
2620:1ec:d::10/128
2620:1ec:d::11/128
2620:1ec:8f0::/46
2620:1ec:900::/46
2620:1ec:a92::152/128
2620:1ec:a92::153/128
2a01:111:f400::/48
2620:1ec:8f8::/46
2620:1ec:908::/46
2a01:111:f402::/48
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select Do Not Agree to exit.